 SIM cards are identified on their individual operator networks by a unique IMSI. Mobile operators connect mobile phone calls and communicate with their market SIM cards using their IMSIs. The format is:
SIM cards are identified on their individual operator networks by a unique IMSI. Mobile operators connect mobile phone calls and communicate with their market SIM cards using their IMSIs. The format is:§ The first 3 digits represent the Mobile Country Code (MCC).
§ The next 2 or 3 digits represent the Mobile Network Code (MNC). 3-digit MNC codes are allowed by E.212 but are mainly used in the United States and Canada.
§ The next digits represent the mobile station identification number. Normally there will be 10 digits but would be fewer in the case of a 3-digit MNC or if national regulations indicate that the total length of the IMSI should be less than 15 digits.
Authentication key (Ki)
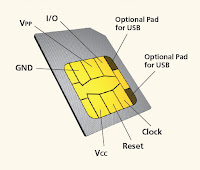 The Ki is a 128-bit value used in authenticating the SIMs on the mobile network. Each SIM holds a unique Ki assigned to it by the operator during the personalization process. The Ki is also stored in a database (known as Authentication Center or AuC) on the carrier's network.
The Ki is a 128-bit value used in authenticating the SIMs on the mobile network. Each SIM holds a unique Ki assigned to it by the operator during the personalization process. The Ki is also stored in a database (known as Authentication Center or AuC) on the carrier's network.The SIM card is designed not to allow the Ki to be obtained using the smart-card interface. Instead, the SIM card provides a function, Run GSM Algorithm, that allows the phone to pass data to the SIM card to be signed with the Ki. This, by design, makes usage of the SIM card mandatory unless the Ki can be extracted from the SIM card, or the carrier is willing to reveal the Ki. In practice, the GSM cryptographic algorithm for computing SRES_2 (see step 4, below) from the Ki has certain vulnerabilities that can allow the extraction of the Ki from a SIM card and the making of a duplicate SIM card.
1. When the Mobile Equipment starts up, it obtains the International Mobile Subscriber Identity (IMSI) from the SIM card, and passes this to the mobile operator requesting access and authentication. The Mobile Equipment may have to pass a PIN to the SIM card before the SIM card will reveal this information.
2. The operator network searches its database for the incoming IMSI and its associated Ki.
3. The operator network then generates a Random Number (RAND, which is a nonce) and signs it with the Ki associated with the IMSI (and stored on the SIM card), computing another number known as Signed Response 1 (SRES_1).
4. The operator network then sends the RAND to the Mobile Equipment, which passes it to the SIM card. The SIM card signs it with its Ki, producing SRES_2, which it gives to the Mobile Equipment along with encryption key Kc. The Mobile Equipment passes SRES_2 on to the operator network.
5. The operator network then compares its computed SRES_1 with the computed SRES_2 that the Mobile Equipment returned. If the two numbers match, the SIM is authenticated and the Mobile Equipment is granted access to the operator's network. Kc is used to encrypt all further communications between the Mobile Equipment and the network.









No comments:
Post a Comment